Assessing Cyber Risk: Metric of the Month
An personnel just lately acquired an electronic mail from me, letting him know that I was in an critical conference and inquiring if he could text me. The only problem was that it was not me. “Fake Perry,” as we connect with the would-be scammer, experienced been messaging our workers in an attempt to get entry to the company’s accounts.
If Phony Perry experienced gotten the employee’s number, the upcoming move would have been to connect with the cellular phone company and have the employee’s number forwarded to his cellular phone, which would have made it considerably easier to hack into our accounts. Many thanks to our employees’ vigilance and the cybersecurity schooling we gave them, no one particular fell for it.
We enjoy building exciting of Phony Perry, but we acquire cybersecurity seriously, and you must, also. Hackers have correctly extracted millions of pounds in ransoms from companies like schools and hospitals. Additional just lately, the Colonial Pipeline hack still left considerably of the southeastern U.S. reeling from fuel shortages and surging fuel selling prices. Cyber-criminals will appear for your group at some point if they have not previously. What are you undertaking to recognize and assess your cyber threats?
Our recent enterprise chance management study requested respondents to recognize the proportion of their top threats that drop into types, which include strategic chance, operational chance, financial chance, and cyber chance. We observed that 1 out of each individual 10 top threats assessed by respondents fell into the cyber chance class, both at the twenty fifth percentile and at the median. Businesses in the 75th percentile mentioned that one particular-fifth of their top threats were cyber threats.
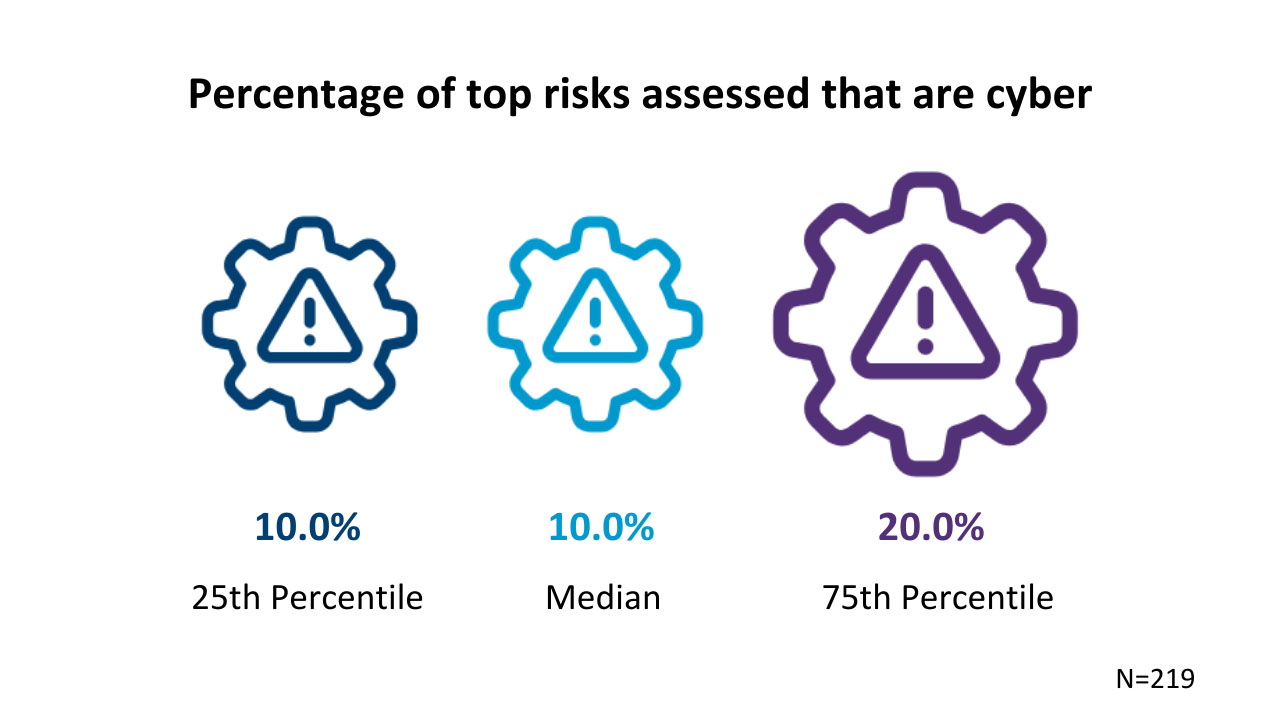
Businesses in the median and twenty fifth percentiles are not necessarily slipping behind — it is superior that cyber chance is at least on their radar. At the identical time, it would make perception for companies to assess extra cyber threats between their top threats, presented the financial and operational destruction these attacks can threaten.
Defending Your Company
Taking actions to handle cyber chance is in each individual organization’s fascination for the reason that it is not a problem of no matter whether, but when, these attacks will arise. And there is no problem that a effective breach of your methods will acquire a financial toll. For that purpose, CFOs and other finance leaders cannot pay for to shrug off planning for cyber chance as just yet another item on It is checklist. Down below, we discuss three tips dependent on the moves we see top businesses building.
1. Make investments in Preparations for Cyber Chance
Committing methods to guard your group towards cyber chance is often a clever expense. It is improved to dedicate these methods upfront to avoid or mitigate assault destruction. Normally, you will shell out on the back conclude the moment the ransom is owing or customers’ info has been compromised. If you have the methods, now is also a superior time to devote in tools that support validate no matter whether vendor payment requests are legitimate and flag suspicious transactions.
Preparing for cyberattacks also signifies schooling workers, so they are common with the normal approaches hackers acquire. Assuming that all workers are savvy adequate to study the indications of an attempted assault could be an expensive mistake. Standard stability characteristics like two-component authentication are very efficient if workers master how to use them.
two. Assess Cyber Chance
At a superior degree, assessing cyber chance appears to be like considerably the identical as any other enterprise chance evaluation. You will need to recognize the regions most inclined to chance and assess no matter whether the present controls and safeguards hold the chance beneath the organization’s degree of chance hunger. Cyber-chance evaluation must also incorporate IT penetration testing and utilizing filtering methods for suspicious or exterior e-mails. Alongside with these actions, make sure you have motion programs so that you are not still left scrambling when an assault has previously happened.
three. Make Certain Policies Are Crystal clear and Workforce Adhere to Them
One particular widespread kind of cyberattack entails seemingly legitimate payment requests from distributors that ask an group to alter the accounts to which payments are made. To make certain that requests from lousy actors really do not get processed, it is important to create distinct treasury guidelines that each individual personnel follows to the letter.
However, we observed by means of our recent treasury research that several companies wrestle in this region. Fewer than 50 {ae9868201ea352e02dded42c9f03788806ac4deebecf3e725332939dc9b357ad} of the respondents to our treasury study described that their group thoroughly communicates treasury policy. That signifies extra than 50 {ae9868201ea352e02dded42c9f03788806ac4deebecf3e725332939dc9b357ad} of respondents most likely really do not do a good occupation building sure treasury guidelines are distinct.
Nearly 50 {ae9868201ea352e02dded42c9f03788806ac4deebecf3e725332939dc9b357ad} of all those surveyed mentioned that workers really do not adhere to the recognized policy very closely possibly. With cyberattacks on the rise, it is simply not worthy of having pointless threats even a one personnel who performs quick and unfastened with the policy could trigger financial destruction.
Given the advancement of cyberattacks and the ensure that they will proceed, it is time to redouble the organization’s initiatives to assess, prioritize, and mitigate cyber threats. Investments in this region will shell out off down the road, possibly by avoiding cyberattacks or lessening the destruction they do. We may well not all be dependable for ensuring that gasoline is flowing to a massive location of the U.S. Continue to, these attacks threaten major destruction to a small business and its shoppers.
Perry D. Wiggins, CPA, is CFO, secretary, and treasurer for APQC, a nonprofit benchmarking and finest tactics research group dependent in Houston, Texas.







